Endpoint Security & XDR by eBuilder Security
eBuilder Security offers Endpoint Security & XDR services for effective detection and prevention against all types of attacks.
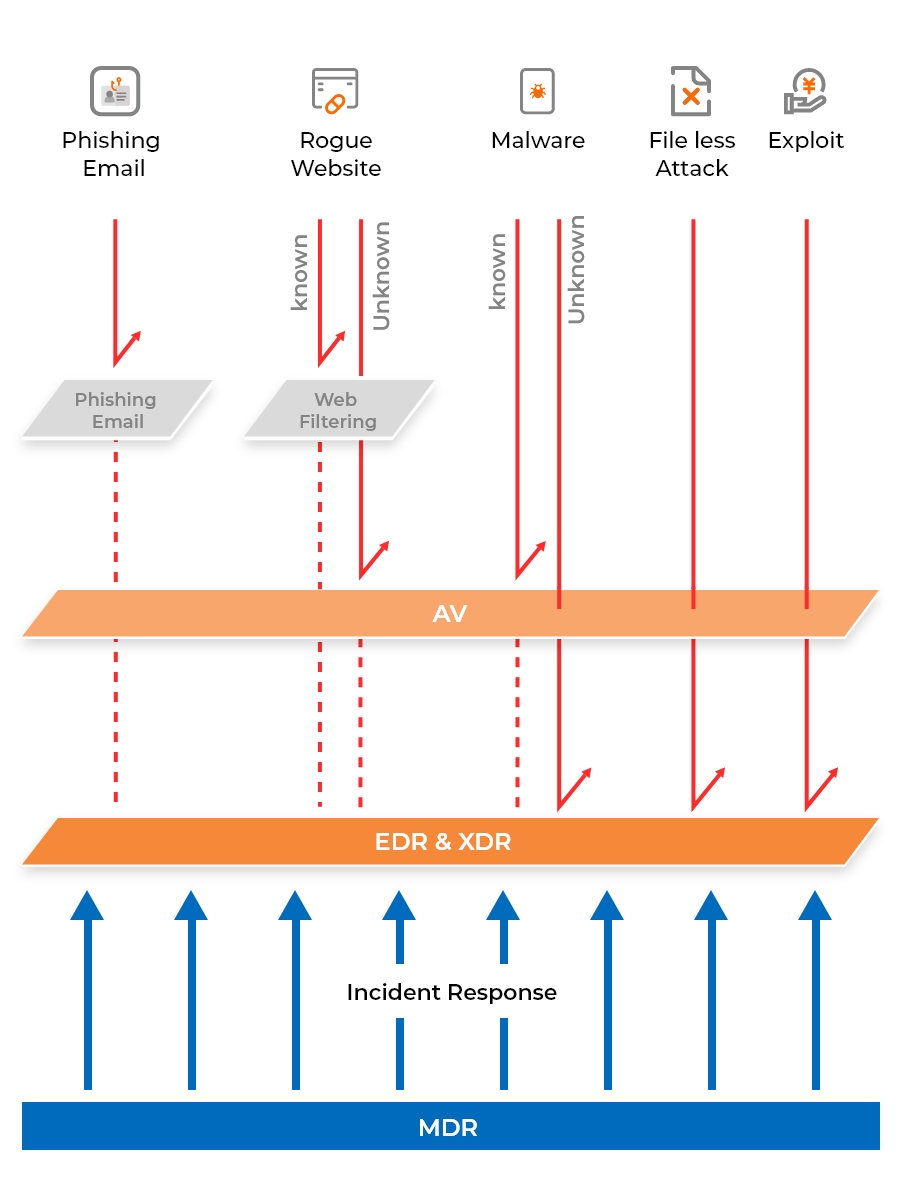
Difference Between Antivirus, EDR, XDR, and MDR
An antivirus program serves as the standard solution for detecting and removing malware from your system. It scans all files and processes to identify malicious content and either deletes or quarantines them automatically.
EDR, or Endpoint Detection and Response, goes beyond the capabilities of an antivirus software, offering comprehensive reporting on the source and progression of malware, along with advanced response features such as automatic host isolation for post-attack cleanup.
XDR, or eXtended Detection and Response, elevates security further by aggregating data from multiple sources, such as EDR, spam filters, firewalls, cloud service authentication logs, and beyond.
MDR or Managed Detection and Response consolidates technology and human expertise to offer EDR and XDR as fully managed services.
Next-Generation Antivirus (NGAV)
Traditional antivirus solutions rely on signature-based detection technology which involves pattern matching against a malware signature database. Modern attacks use more advanced and sophisticated technologies to avoid traditional antivirus such as fileless malware, changing malware signatures, and encryption.
Next-Generation Antivirus (NGAV) utilizes a combination of technologies such as artificial intelligence (AI), machine learning, behavioral detection and exploit protection to prevent known and unknown threats including advanced malware, ransomware, and zero-day attacks. Realtime protection offered by NGAV quickly identify and neutralize threats before they cause any harm.
Endpoint Detection and Response (EDR)
While NGAV acts as the first line of defense that prevents attacks, no solution is 100% perfect, and some attacks can breach the defenses and penetrate the network. If this goes undetected, attackers can even spend months in your network and also move laterally, causing more and more damage. This is where an EDR solution becomes important.
Endpoint Detection and Response (EDR) is a security solution that continuously monitors the end-user devices in real-time in order to detect the threats that come through those endpoints. Using advanced analytics and actionable intelligence, EDR can detect malicious activities, promptly alert security teams, provide remediation measures, and contain an attack.
Some additional Capabilities that EDR provides:
- Advanced Behavioral Analytics
- Threat Hunting
- Incident Investigation
- Customizable Security Policies
- Deep Forensic Analysis
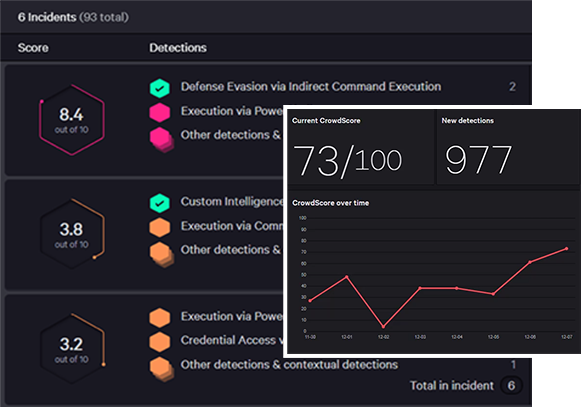
Advanced Endpoint Protection with both NGAV and EDR
Unifying Next-Generation Antivirus (NGAV), the prevention component, with Endpoint Detection and Response (EDR), the detection component, eBuilder Security offers complete protection for your endpoint devices against advanced threats.
Our solution:
- Stops breaches with the industry’s fastest deployment times
- Provides real time protection and continuous monitoring against security threats and incidents
- Accelerates investigation and remediation of security incidents
- Ensures that stealthy attacks don’t go undetected 24/7
- Facilitates malware removal and clean up infected endpoints to prevent further spread
- Uses behavioral analysis to identify suspicious activities and anomalies indicative of emerging threats
- Provides a holistic view of your threat landscape, and real-time and historical visibility across endpoint events and activities
Unified Platform for Detection and Response
Using multiple security solutions to detect and mitigate threats within the IT environment leads to data silos. These isolated datasets lack correlation with other data, resulting in missing out on the broader context that is required for a full understanding and effective response to threats. Manually correlating and analyzing data from multiple tools is error-prone and also resource and time intensive work.
That’s why organizations need a unified approach to threat detection and response by integrating data from various sources in the IT environment. XDR, or Extended Detection and Response is a solution built to cater this requirement by collecting and correlating security telemetry from multiple layers of the IT infrastructure.
XDR – Extended Detection & Response
XDR significantly extends beyond the scope of EDR and other individual security tools by gathering and consolidating data from various sources such as endpoints, networks, cloud services, email, and more to offer a unified and holistic view of the threats faced by the organization. XDR uses advanced analytics and automation to detect sophisticated attacks, prioritize alerts, and facilitate faster and effective incident response through a single consolidated console.
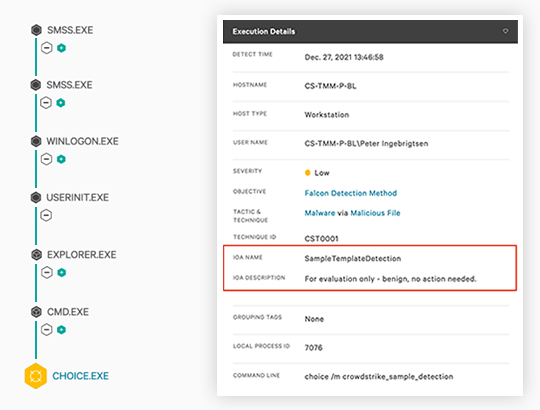
Benefits of XDR:
- Comprehensive and cross-layer threat visibility
- Reduced noise and alert fatigue through prioritization
- Faster and automated response
- Enhanced threat intelligence
- End to end incident response streamlining
Threat Hunting
As cyber threats become increasingly advanced and elusive, the need to proactively hunt for threats and stay one step ahead of attackers is becoming more and more important. Proactive threat hunting actively seeks out hidden and emerging threats including zero-day exploits and insider threats, ensuring early detection and mitigation. Human expertise and intuition employed in threat hunting facilitate the identification of even the subtle signs of a potential threat and tailor the investigations to focus on the factors unique to your organization.
Although there are several important reasons to conduct threat hunting, finding adequate personnel who are competent in this area is challenging and also expensive. As a solution, you can obtain threat hunting as a managed service and utilize the deep expertise of seasoned threat hunters 24/7 at a more affordable cost.
Our partners for Endpoint Security and XDR
CrowdStrike, a global cybersecurity leader, has redefined modern security with one of the world’s most advanced cloud native platforms for protecting critical areas of enterprise risk – endpoints and cloud workloads, identity, and data.
CrowdStrike offers complete Endpoint security solutions by providing real-time threat protection, detection, and automated response. Falcon XDR elevates EDR capabilities to the next level by extending beyond your endpoint devices, across your security stack. Falcon OverWatch provides Proactive Threat Hunting with 24×7 human vigilance and complete attack analysis with immediate, actionable alerts.
eBuilder Security, partnered with CrowdStrike ensures unmatched capabilities across your security stack through breach prevention, detection, and response.
Learn More about CrowdStrike Services
Recognized as a leader in the Gartner Magic Quadrant, Cybereason provides complete protection through a unified security approach securing all endpoints, fixed or mobile. Cybereason EDR focuses on ending malicious operations before they take hold on endpoint devices, eliminating the traditional alert-centric process. Cybereason XDR expands these managed detection and response capabilities across your entire technology stack, not just endpoints. Detection and remediation of threats take only seconds to minutes, ensuring that threats are mitigated before they become breaches.
Partnered with Cybereason, eBuilder Security, offers top-notch detection and response services managed and administered for your convenience with a number of hosting options for you to choose from.
Multiple Hosting Options
We offer different hosting options for you to choose from depending on the nature of your business and the compliance and regulatory requirements you need to adhere to. You can select the best hosting solution that suits your unique needs.
- Public cloud hosting
- Private cloud hosting
- On-Premises hosting

Our Managed Service - MDR
Unburden yourself with the administration and management of Detection and Response services and be totally hands off while we manage them for you. eBuilder Security, provides top-notch, continuous Managed Detection and Response (MDR) Services, tailored to address all security risks threatening your systems.
eBuilder Security Managed Services deliver affordable, subscription-based, world-class quality services tailored for specific security issues.
Let us take care of your security so you can fully focus on your core operations.
What Our Clients Say
“Cybersecurity has top priority in our firm. Our software is installed on Exchanges and Central Depositories around the World. We chose eBuilder Security because of their extended experience in delivering secure SaaS to global organizations.
We are very happy with their professionalism and customer service.”
Frequently Asked Questions
What is an endpoint?
An endpoint is any device or node that connects to a corporate network and communicates with other devices over that network. Following are some examples of endpoints:
- Computers e.g., Desktops, Laptops, servers
- Mobile devices e.g., Smartphones, Tablets
- Networked Printers and Scanners
- Internet of Things (IoT) devices e.g., smart devices, voice assistants
- Other devices that communicate with the central network
What is endpoint security?
Endpoint security (also known as ‘endpoint protection’) is the cyber security practice of safeguarding endpoints such as computers, and mobile devices from various cyber security threats.
Endpoints are often subjected to attacks by cybercriminals who try to gain unauthorized access to sensitive data or the underlying network. Endpoint security plays an important role in overall network security as a well-executed endpoint security strategy can prevent and detect threats before they spread over the network.
Is EDR suitable for small organizations as well as large enterprises?
EDR solutions are scalable and can also be tailored to fit any size of an organization be it a small business or a large enterprise. Organizations with limited internal resources usually go for managed EDR services provided by managed security service providers (MSSPs) to offload the administrative and management overhead of their EDR solution.
What types of threats can EDR defend against?
EDR solutions are designed to defend against a wide range of security threats such as malware, zero-day exploits, advanced persistent threats (APTs), phishing attacks, fileless attacks, insider threats, unauthorized data exfiltration, Command and Control (C2) Communications, Behavioral Anomalies, and Data Loss Prevention (DLP).

Let us show you how we can help your organization
For starters, we can show how to improve upon your existing security in 30 mins. Care to proceed?

