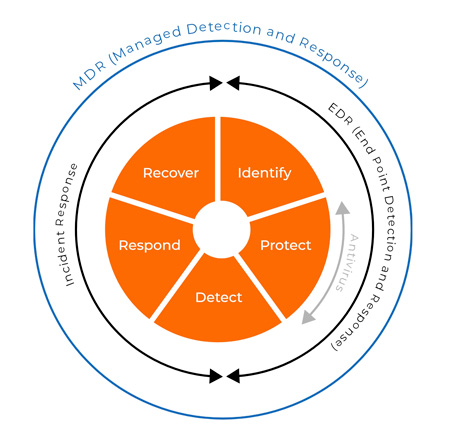
Managed Detection and Response
Attackers don’t take breaks and neither do we. As a trusted CrowdStrike partner, we offer CrowdStrike Managed Endpoint Detection & Response (EDR) with 24/7 Threat Hunting.
Managed Detection and Response (MDR)
With MDR, we significantly widen the capabilities of CrowdStrike EDR by combining technology with human expertise to perform threat hunting, monitoring, and response. You can quickly detect and minimize the impact of threats with our MDR service without a dedicated security operations team.
eBuilder Security’s MDR service includes the service of Security Operations Center (SOC) to monitor threats in real time. Our MDR service extends the capabilities of SOC by managing the detected threats and response, and also the management of your Crowdstrike environment. Our MDR service can isolate threats and prevent them from spreading. It can also assist you with the remediation steps that need to be performed.
- 24/7 continuous monitoring and response
- Experienced security analysts oversee your organization’s defenses without adding full-time staff and resources
- Proactive management and optimization
- Investigates all detections: critical, high, medium, low
- SOC (Security Operations Center) services
Security Operations Center (SOC)
Attackers take no time-outs. Organizations may be vigilant during regular business hours, however, attackers are not limited by time boundaries. In fact, attackers are more likely to strike outside normal business hours and on weekends, as they are aware that organizations lack monitoring and support and therefore, are more vulnerable during these times, considerably increasing their likelihood of success.
Therefore, to overpower cybercriminals and to secure organizational data and infrastructure, 24/7 monitoring is a must. This is where we can help you out. eBuilder Security’s SOC service continuously monitors your organization’s IT systems 24/7 for threats and escalates them immediately.
- 24/7 continuous threat monitoring
- Faster response times
- Reducing the risk of a breach
- Affordable and scalable
- Reducing the burden on internal SecOps teams

Threat Hunting Key Features
- Attacker mentality: Effective threat hunting requires the ability and expertise to think like an attacker.
- Cross-disciplinary expertise: Our solution employs a team of elite experts from a wide range of backgrounds, including government, law enforcement, commercial enterprise, the intelligence community, and defense.
- 24/7/365 availability: When a sophisticated intrusion occurs, time is critical. Your adversaries do not sleep and are not restricted by time zones or geography — and neither should your threat hunting team.
- Continuous vigilance: Our solution continuously and proactively delivers results every minute of every day.
Our Process
Collect
Detect
Analyze
Report
Remediate
About CrowdStrike
CrowdStrike, a global cybersecurity leader, has redefined modern security with one of the world’s most advanced cloud native platforms for protecting critical areas of enterprise risk – endpoints and cloud workloads, identity, and data.
CrowdStrike Falcon OverWatch: 24/7 Proactive Threat Hunting
Falcon OverWatch™ is CrowdStrike’s managed threat hunting service, built on the CrowdStrike Falcon® platform. OverWatch provides deep and continuous human analysis, 24/7, to relentlessly hunt for anomalous or novel attacker tradecraft that is designed to evade standard security technologies. Armed with cloud-scale telemetry and detailed tradecraft on more than 130 adversary groups, OverWatch provides an unparalleled ability to see and stop the most advanced threats.
What Our Clients Say
“Cybersecurity has top priority in our firm. Our software is installed on Exchanges and Central Depositories around the World. We chose eBuilder Security because of their extended experience in delivering secure SaaS to global organizations.
We are very happy with their professionalism and customer service.”
Frequently Asked Questions
Why would eBuilder Security MDR be necessary if an organization has an EDR already?
eBuilder Security MDR does not look for your low-level commodity malware (the EDR does that well enough). Instead, it looks for the less obvious/more dangerous threats.
eBuilder Security MDR proactively hunts for these types of threats in the client’s systems and provides remediation recommendations and detailed analytics that tells the customer what just happened and how to respond to the attack.
Does eBuilder Security MDR perform an initial assessment of the environment before starting investigations?
No, an initial assessment is not necessary with eBuilder Security MDR. When investigating, we compare the various activities of users, processes, or workstations in the customer’s environment.
What is the benefit of using eBuilder Security MDR as a managed service with SOC?
Our SOC will give you remediation 24/7/365, or else you would need someone to be seated, waiting for MDR or the regular EDR to alert. With eBuilder Security SOC we do that for you.
What is the difference between MDR and Managed SIEM?
Security information and event management (SIEM) is a broad category of technology that works by gathering data from different security devices and analyzing them to detect any anomalies. The scope of SIEM services can differ vastly after that first step. Some are technology-only solutions while others are more like managed event processing and alerting services.
One issue common to all SIEM customers is that they face difficulties in understanding the results exposed by SIEM data. Almost 45 percent of SIEM customers say that they are deficient in in-house expertise to get the most out of their SIEM solution. Also, SIEMs can be expensive and resource-intensive. MDRs, on the other hand, are distinguished due to their light network footprint and quick time-to-value.

Let us show you how we can help your organization
For starters, we can show how to improve upon your existing security in 30 mins. Care to proceed?

